The Future is
Bleak
Brilliant
Uncertain
Promising
Hopeful
Bright
Luminous
The Future is Bleak
- Cyber attacks have increased by 38% year-over-year, with ransomware attacks occurring every 11 seconds
- Average cost of a data breach has reached $4.88 million globally, with some breaches costing hundreds of millions
- Web applications face an average of 94 attacks per day, targeting common vulnerabilities like injection flaws and broken authentication
- Supply chain attacks have tripled in the past year, affecting thousands of downstream organizations through compromised dependencies
- 88% of successful cyber attacks are due to human error, highlighting the critical need for automated security measures
Current Threat Landscape
The Future is Uncertain
- OWASP Top 10 vulnerabilities remain prevalent, with injection attacks and broken access control leading the list
- Modern web applications use dozens of third-party libraries, each potentially introducing security risks
- DevOps speed often conflicts with security thoroughness, creating gaps in the development lifecycle
- Remote work has expanded attack surfaces, making traditional perimeter security insufficient
- Security skills shortage means many organizations lack dedicated security expertise to properly assess risks
Web Application Vulnerabilities on the Rise
The Future is Promising
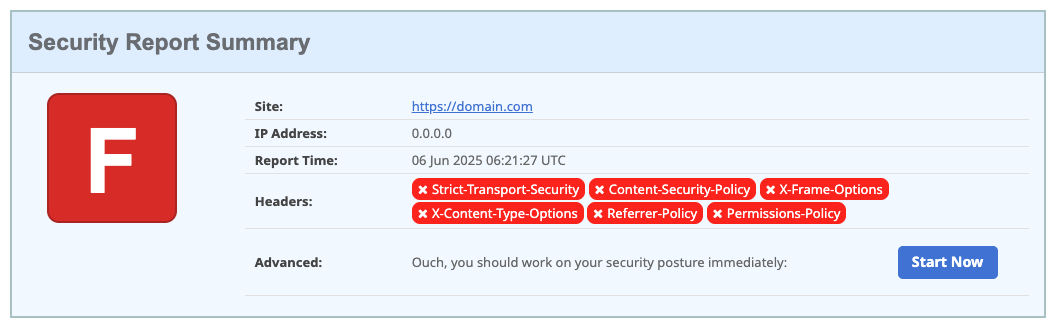
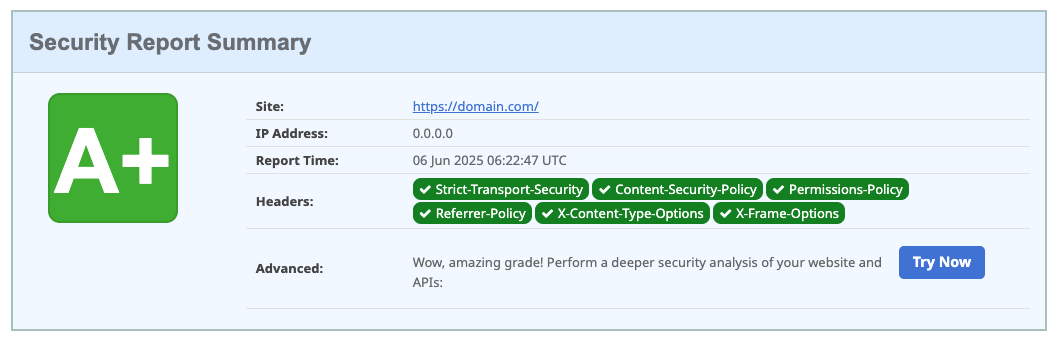
- Content Security Policy (CSP) prevents XSS attacks by controlling which resources browsers can load and execute
- HTTP Strict Transport Security (HSTS) forces secure HTTPS connections and prevents protocol downgrade attacks
- X-Frame-Options and X-Content-Type-Options headers protect against clickjacking and MIME-type confusion attacks
- Referrer Policy controls how much referrer information is shared, protecting user privacy and preventing information leakage
- Implementation is straightforward and provides immediate protection with minimal performance impact
Essential HTTP Security Headers
The Future is Promising
Example: Before
The Future is Promising
Example: After
The Future is Hopeful
- Subresource Integrity (SRI) uses cryptographic hashes to verify that external resources haven't been tampered with
- npm audit automatically scans Node.js dependencies for known vulnerabilities and provides upgrade recommendations
- Dependency scanning catches compromised packages before they enter your codebase, preventing supply chain attacks
- Regular dependency updates and security patches reduce exposure to known vulnerabilities
- Automated dependency monitoring provides continuous visibility into your application's security posture
Subresource Integrity & Dependency Security
The Future is Bright
- SonarQube and Sonar Cloud provide comprehensive code quality and security analysis, catching vulnerabilities during development
- Semgrep offers advanced static analysis with custom rules for specific security patterns and compliance requirements
- Integration with CI/CD pipelines ensures every code change is automatically scanned for security issues
- Real-time feedback helps developers learn secure coding practices while they work
- Shift-left security approach catches vulnerabilities early when they're cheapest and easiest to fix
Static Code Analysis & Advanced Scanning
The Future is Brilliant
- Security headers implementation and configuration, including CSP policies tailored to your applications
- Semgrep and/or SonarQube setup and integration with development workflows and CI/CD pipelines
- Initial security assessments and baseline establishment to understand current security posture
- Configuration and setup of ongoing security testing platforms like Detectify or Probely for continuous monitoring
- Developer training and documentation to ensure your team can maintain and improve security measures over time
Our Security Implementation Services
The Future is Luminous
- We implement the foundational security tools: headers, CSP, static code analysis with Semgrep and Sonar
- Partner with industry-leading platforms like Detectify or Probely for ongoing vulnerability scanning and penetration testing
- Our role: setup, configuration, initial scans, and knowledge transfer to your team
- Third-party specialists handle continuous monitoring, ensuring comprehensive coverage without overwhelming your resources
- This hybrid approach gives you both immediate implementation expertise and long-term automated security monitoring
Your Complete Security Solution
Ready to Start Your Security Journey?
Let's discuss how we can implement these security measures for your organization
The Future is
Bleak
Brilliant
Uncertain
Promising
Hopeful
Bright
Luminous
security
By Mads Stoumann
security
- 25



