Book 3. Operational Risk
FRM Part 2
OR 9. Case Study- Cyberthreats and Information Security Risks

Presented by: Sudhanshu
Module 1. Information Security Risks & Frameworks
Module 1. Information Security Risks & Frameworks

Topic 1. Information Security Risk Typology
Topic 2. Cybersecurity Risk Frameworks and Standards
Topic 3. NIST CSF
Topic 4. CIS
Topic 5. ISO
Topic 6. Cybersecurity Protection and Monitoring
Topic 7. Equifax Case Study






Topic 1. Information Security Risk Typology
-
Information security risk encompasses more than just cyber risk and includes both intentional and unintentional actions.
-
Intentional Actions: Employees stealing/leaking data, external parties hacking emails.
-
Unintentional Actions: Losing or accidentally disclosing private information, inadvertently sending sensitive data.
-
-
Also includes loss/theft of non-digital data (e.g., paper documents).
-
Firms are responsible for implementing adequate risk controls.
-
Categorizes data incidents based on four-quadrants approach (two dimensions): Internal vs. External and Intentional vs. Unintentional
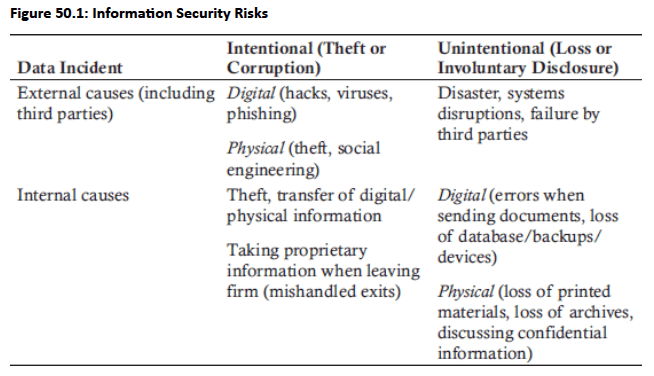
- Industry Vulnerability: Financial industry faces particular susceptibility to cyberattacks and information leaks beyond general information security risks
- High-Profile Incidents: Notable 2017 data breaches including Equifax and Appleby (offshore law firm) highlighted inadequate risk defense vulnerabilities across multiple sectors
- COVID-19 Acceleration: Pandemic intensified digital protection needs by speeding digitization pace (QR codes), accelerating social media use, and disrupting supply chains
- Cross-Sector Impact: Significant data leaks affected diverse industries including insurance, journalism, and cryptocurrencies, demonstrating widespread exposure
- Defense Inadequacy: Recent incidents underscore the critical need for stronger cybersecurity measures and comprehensive information protection strategies
Topic 1. Information Security Risk Typology
Practice Questions: Q1
Q1. The four-quadrant approach categorizes information security risks as:
A. internal versus external and intentional versus unintentional.
B. internal versus external and in house versus third party.
C. intentional versus unintentional and digital versus physical.
D. intentional versus unintentional and theft versus corruption.
Practice Questions: Q1 Answer
Explanation: A is correct.
The four-quadrant approach analyzes information security risks with data incidents categorized as internal versus external and intentional versus unintentional. Theft and corruption are part of intentional data incidents. Both intentional and unintentional data incidents can be categorized as digital or physical. In-house and third-party incidents are just examples of internal and external data incidents, respectively.
Practice Questions: Q2
Q2. An employee inadvertently emails a sensitive and confidential file to a third-party recipient. The employee's action would most likely be categorized as:
A. internal and intentional.
B. external and unintentional.
C. internal and unintentional.
D. external and intentional.
Practice Questions: Q2 Answer
Explanation: C is correct.
Errors when sending documents, including sending the wrong attachments or sending to the wrong email recipients, are examples of internal and unintentional data incidents.
Practice Questions: Q3
Q3. Following a severe power outage, a firm is unable to recover one of its servers that had significant and sensitive client information. This incident would most likely be categorized as:
A. internal and intentional.
B. external and unintentional.
C. internal and unintentional.
D. external and intentional.
Practice Questions: Q3 Answer
Explanation: B is correct.
Disaster, systems disruptions, and third-party failures are examples of external and unintentional data incidents.
Topic 2. Cybersecurity Risk Frameworks and Standards
- Cyber risk is one of the most important information security risks.
-
Three primary standards/frameworks for cyber risk:
-
U.S. National Institute of Standards and Technology Framework for Improving Critical Infrastructure Cybersecurity (NIST CSF).
-
Center for Internet Security (CIS) Critical Security Controls.
-
International Standards Organization (ISO) framework ISO 27001.
-
Topic 3. NIST CSF
-
Founded by U.S. Congress and operates under the U.S. Department of Commerce.
-
Initially developed for critical infrastructure (e.g., power plants), now applicable to any business.
-
Voluntary framework.
-
Helps businesses analyze, assess, and reduce threats/vulnerabilities.
-
Assists with response and recovery post-incident (root-cause analysis).
-
Similar to an Operational Risk Management Framework (ORMF) that identifies, assesses, mitigates, and monitors risks.
-
Identify:
-
List all IT/technology equipment, software, and data (electronic, mobile, POS).
-
Businesses should create and share cybersecurity policy, including roles/responsibilities of employees, vendors, third parties and outline steps for cyberattack scenarios.
-
-
Protect:
-
Businesses should restrict network and device access, and use security software for protection, encryption, and data backup.
-
Implement policies for safe disposal of files and data.
-
Regularly update security software and train employees on risk mitigation roles.
-
-
Detect:
-
Businesses should monitor computers, software, and hardware for unauthorized access/users/connections.
-
Investigate unusual activities.
-
-
Respond:
-
Businesses should create a plan for maintaining operations during an attack.
-
Notify customers, employees, and stakeholders.
-
Investigate, contain, and report attacks to law enforcement.
-
Update cybersecurity policies with lessons learned.
-
Prepare for unpredictable events (e.g., power outage).
-
-
Recover:
-
Businesses should repair and restore impacted equipment/data post-attack.
-
Ensure continuous and adequate information flow to employees and customers.
-
Topic 3. NIST CSF
-
Critical Security Controls (CIS) Overview
-
Detailed guidance for establishing or reviewing cybersecurity protocols.
-
Can complement existing compliance standards (e.g., NIST) or aid ISO 27001 certification.
-
Protects firms from widespread cyberattacks and threats.
-
Includes continuously updated key controls by experts.
-
Mapped to and referenced by various legal, regulatory, and policy frameworks.
-
Refreshed to incorporate cloud computing, virtualization, mobility, outsourcing, and remote work.
-
Topic 4. CIS
-
ISO 27001 Overview
-
Key global standard for cybersecurity.
-
Provides guidance on:
-
Organization of risk management activities.
-
Operational planning and control.
-
Information security risk assessment and treatment.
-
Governance, policies, communications, management review, and audit.
-
-
Does not provide direct implementable advice but acts as a checklist for certification.
-
Firms need an Information Security Management System (ISMS) to manage risks.
-
Requires effective, comprehensive controls and ongoing improvements in risk management.
-
Topic 5. ISO
-
Components of Cybersecurity Information Protection (CIA)
-
3 components: Confidentiality, integrity and availability
-
Confidentiality and integrity relate to information security, while availability relates to business continuity.
-
-
Information Controls: Behavioral vs. Technical
-
Behavioral Controls: Address human behavior and shortcomings.
-
Aim at protecting information through awareness campaigns, rules of conduct, training, password management, and appropriate supervision and necessary sanctions.
-
-
Technical Controls: Address the technical side of risk through prevention, detection, and mitigation.
-
Preventative Controls: Directed at external threats, and include firewalls, encryption, passwords, and patching.
-
Detective Controls: Try to generate early warnings of data incidents, including data loss prevention and detection (DLPD) solutions that monitor and identify unauthorized data disclosures.
-
Mitigating Controls: Try to keep redundancies and backups offline.
-
-
-
Risk Monitoring and Departmental Structure
-
Firms must conduct cost-benefit analysis for controls (cost, convenience, speed vs. risk reduction).
-
Most firms monitor cyberattacks within their IT department.
-
Many firms have a separate information security department responsible for designing, maintaining, and monitoring risk controls.
-
Topic 6. Cybersecurity Protection and Monitoring
Topic 7. Equifax Case Study
-
The Equifax Cyber Breach (2017)
-
Equifax: One of the three main credit bureaus in the U.S.
-
Major cyber breach in March 2017, one of the largest in recent years.
-
Attackers exploited a vulnerability in an Apache Struts patch.
-
Gained access to customer names, addresses, birthdays, Social Security numbers, and credit cards.
-
Attack went unnoticed for three months.
-
Impacted 147 million customers.
-
-
Reasons for Equifax's Vulnerability
-
Used outdated cybersecurity frameworks and policies.
-
Did not adequately update outdated security tools.
-
Internal audit (2015) revealed a backlog of 8,500 unpatched vulnerabilities.
-
Experienced a previous breach in 2016 (430,000 customers impacted).
-
Apache Struts vulnerability had a NIST score of 10 (maximum criticality).
-
-
Five Areas of Weakness at Equifax
-
It maintained insufficient inventory of its IT systems and assets, exposing it to vulnerabilities including the inability to patch systems quickly.
-
It failed to enforce its patch management policy (part of risk management).
-
Employee communication was inefficient and insufficient, as communications about the vulnerabilities missed key employees.
-
Equifax used an expired SSL certificate, which prevented it from adequately monitoring its encrypted traffic. It was only in late July 2017 that the breach was discovered- more than three months after it initially happened.
-
Public/external communication was poor, with weak crisis communication. Equifax
did not alert the public until September 7, 2017.
-
-
Consequences
-
Equifax faced major fallout, including a stock price drop and executive resignations (CEO, CSO, CIO).
-
The company paid $700 million in fines and compensation, with $300 million going to affected individuals.
-
The breach led to a complete overhaul of Equifax’s IT security and leadership structure.
-
Topic 7. Equifax Case Study
Practice Questions: Q4
Q4. Which of the following issues was not identified as a key weakness in Equifax's information security management?
A. Poor public communication.
B. Using an expired digital certificate.
C. Lack of a comprehensive list of its IT assets.
D. Lack of sufficient internal phishing exercises.
Practice Questions: Q4 Answer
Explanation: D is correct.
A lack of sufficient phishing exercises was not one of the key concerns identified in the case of Equifax. Key weaknesses included the following:
- An insufficient inventory of its IT systems and assets
- Failure to enforce its patch management policy
- Inconsistent employee communication
- Using an expired SSL certificate
- Poor public/external communication